Due to the progressive nature of the digitalization of our world, cybersecurity, cyber threats, and cyber risks have piqued the interest of many tech enthusiasts, academics, and cybersecurity experts. Cybersecurity remains, however, a necessity and an indispensable approach serving the nature of modern humankind. Cyber threats have evolved alongside the growing path of digitalization, and the term “cyber risks” remains a hallmark and a reminder for both individuals and organizations to remain vigilant, proactive, and adaptive in their defense strategies. As the digital landscape expands, so too does the sophistication of adversaries, employing advanced tactics that exploit not only technical vulnerabilities but also human behavior.
What is Cyber Risk?
Although defining cyber risk may appear overwhelming due to the complexity and diversity of the field, the most effective way to narrow its definition is to recognize that cyber risk is deeply intertwined with cyber threats and vulnerabilities. Each threat (or potential threat) constitutes a cyber risk. To reduce such risks and prioritize safety, cybersecurity experts develop and strengthen robust methodologies, ensuring systems and processes are fortified against potential breaches. Minimizing risk and fostering a culture of protection are not only preventive measures but also essential steps toward building resilience against any threat or harm.
The Elements of Cybersecurity Risk
To better understand the elements of cybersecurity risk, we present a simple yet effective formula that aids in comprehending the nature of cyber risk:
Cyber Risk = Threat × Vulnerability × Impact
The first component of cyber risk is what we call a threat. Threats refer to any harmful or potentially damaging event to a system. Malware, such as ransomware attacks, which cybercriminals often use to block access to computer systems and cripple operations until a ransom is paid, are examples of threats that can cause severe disruption within an organization.
The second component, vulnerabilities, often referred to as “open doors” for cybercriminals, is closely linked to security gaps. When updates or patches have not been applied, they become vulnerabilities, essentially invitations for attackers to exploit and turn into chaos. For instance, unpatched systems or outdated software can lead to data breaches, malicious activities, and other damaging consequences, often triggering cascading effects across the organization.
Finally, impact refers to the overall consequences when a threat successfully exploits a vulnerability. This impact represents the actual damage, which can range from financial losses and reputational harm to operational downtime and widespread disruption.
Noteworthy, when the complete formula exists within an organization or business, so does the cyber risk. It is imperative to understand that cyber risk extends beyond technical issues, reaching a critical point where national security itself becomes fragile.
Why Cyber Risk Is More Than a Technical Issue
Therefore, collectively, we must acknowledge and understand that the notion of cybersecurity has long ceased to belong to the realm of science fiction or to be seen merely as a technical concern. It has rapidly evolved into an essential pillar for safeguarding not only our digital assets but also the stability, resilience, and well-being of our society as a whole.
To strengthen our point, we turn to the field of critical infrastructure, where cybersecurity plays a crucial role in ensuring that our daily activities can continue uninterrupted and protected. In our latest e-book “How Much Cyber Risk Are You Willing to Accept?”, we have highlighted ten major cyberattacks targeting different critical infrastructure sectors. Unfortunately, some of these incidents had devastating consequences, causing nearly irreparable damage. The impacts extended far beyond the immediate targets, affecting not only the regions and countries where the attacks occurred but also escalating into matters of national security, where the safety of numerous organizations and civilians was placed at risk.
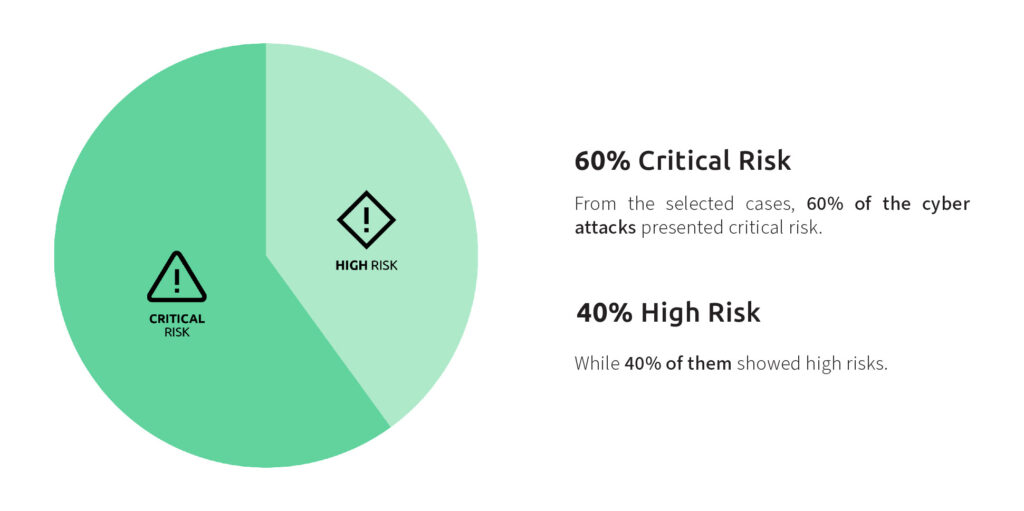
A worrying finding from our study reveals that, out of the major cyberattacks analyzed, 60% were classified as posing a critical risk, while the remaining 40% were assessed as high risk. Considering that our study focuses on the critical infrastructure sector, this result is a stark reminder of just how vulnerable the systems we rely on every day truly are. When services that keep our lights on, water running, and hospitals operating are at such high risk, the consequences go far beyond inconvenience; they threaten people’s safety, livelihoods, and trust.
Furthermore, a common pattern emerged among the cyberattacks featured in our e-book: ransomware played a significant role, appearing in 40% of the cases analyzed. Even within the critical infrastructure sector, ransomware remains a favored tactic for cybercriminals, largely because it offers them high rewards with relatively low risk. Its ability to quickly disrupt essential services and pressure victims into paying large sums makes it a persistent and dangerous threat in today’s cybersecurity landscape.
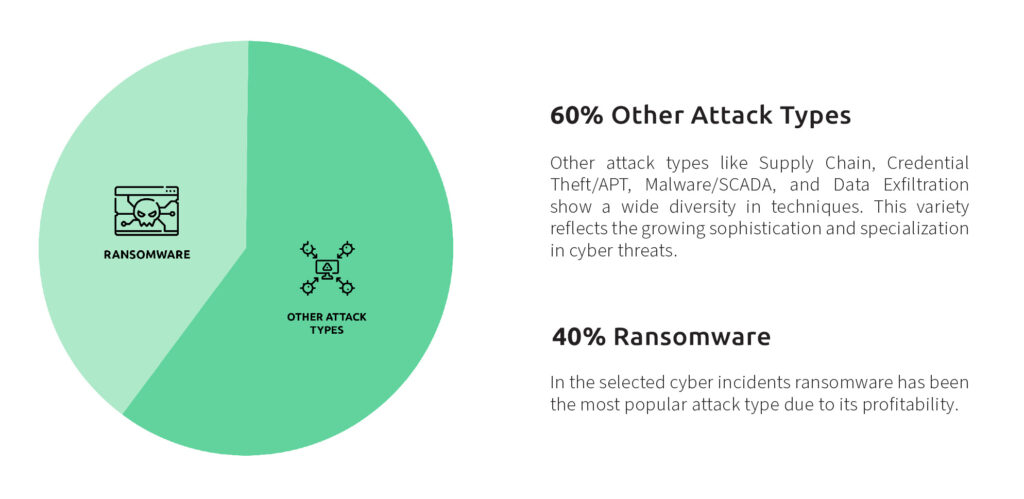
However, other types of attacks are also growing in both number and sophistication, evolving rapidly alongside the cyber landscape itself. To truly grasp the consequences of cyber risk, it is essential to examine the damage these threats can inflict, not only on individual organizations but also on entire critical infrastructure sectors whose disruption can have far-reaching effects on society.
The Consequences of Cyber Risk on the Critical Infrastructure
Critical infrastructure refers to the essential systems and services that underpin the functioning of any society. Neglecting cybersecurity, particularly in relation to critical infrastructure, risks causing a rupture at the very core of societal stability. The consequences of such a failure would extend far beyond mere technical disruption; they could lead to loss of life, large-scale societal disruption, and the collapse of essential services. Disasters of this magnitude would erode public trust, undermine confidence in institutions, and inflict severe economic damage, potentially destabilizing entire regions. The cascading effects could impair emergency response capabilities, disrupt supply chains, and jeopardize national security, leaving lasting scars on both the social and economic fabric.
The economic repercussions of our selected cyber attacks raise an alarming concern regarding cybersecurity measures, particularly in the critical infrastructure area:
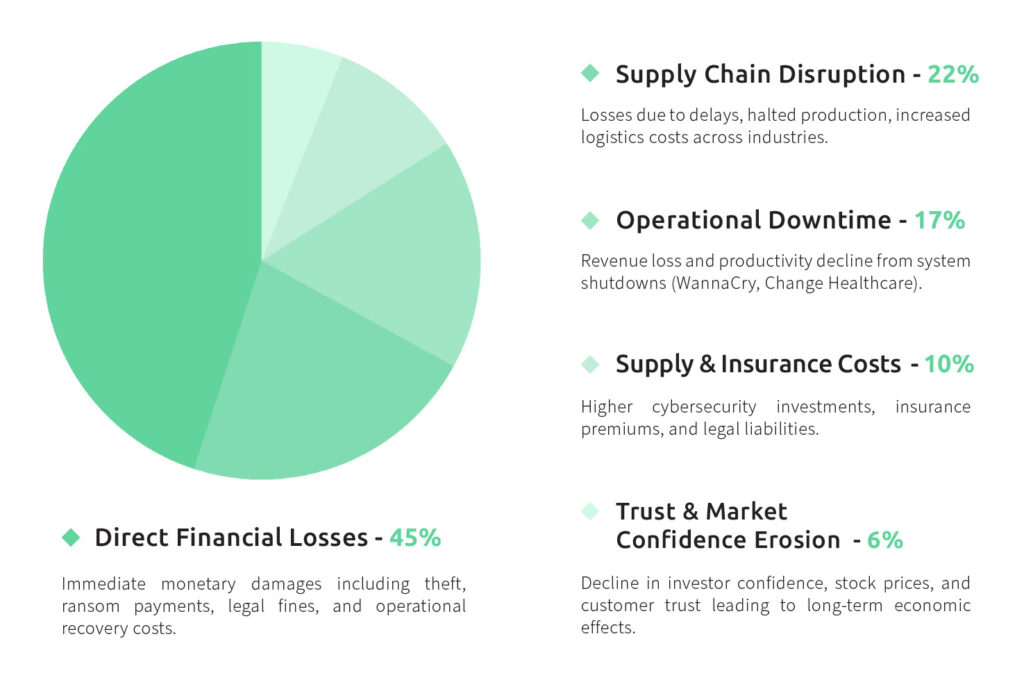
From our selected cases, the figure above illustrates the immediate and tangible impacts experienced in the aftermath of the attacks. It clearly shows the harmful effects on economic stability, with substantial financial losses being one of the most prominent and measurable consequences.
Examples of Cyber Risk Exploitation
The following four cases from our study illustrate how such exploitation can lead to severe consequences, particularly within critical infrastructure. Risk exploitation occurs when cybercriminals have entered ‘the opened doors’ mentioned earlier (vulnerabilities) and manage to breach systems.
- Ukraine Power Grid Attack
In this massive cyberattack, cybercriminals demonstrated how effective malware can be when used to exploit vulnerabilities in the critical infrastructure sector, leaving thousands of organizations and civilians without electricity.
- SolarWinds Supply Chain Attack
In this shocking cyber attack, software supply chain vulnerabilities were exploited, compromising an entire platform, allowing cybercriminals to ‘navigate’ under the radar for months.
- Colonial Pipeline Ransomware Attack
Perhaps one of the most successful ransomware attacks ever made on the critical infrastructure sector. Network vulnerabilities were exploited, forcing a shutdown of fuel distribution and causing an economic disaster followed by societal disruption.
- Bangladesh Bank Heist
Perhaps one of the most notorious cyber-heists in modern history, this case once again reminded us of the severe consequences cyber risks can bring. It exposed critical vulnerabilities in the global banking sector, highlighting just how high the stakes can be.
You can discover more insightful details concerning the major cyber attacks selected in our e-book. Download now and learn to identify risks and protect your business from possible threats.
Proactive Measures for Cyber Risk Mitigation
Protective measures are essential tools for minimizing cyber risks, and their consistent enforcement and continual improvement cannot be emphasized enough. Here are some practical cybersecurity measures to be considered:
- Risk Assessment: Take a close look at your systems to spot vulnerabilities and threats so you can focus your security efforts where they matter most.
- Incident Response Plans: Have clear, step-by-step procedures ready to quickly detect, respond to, and recover from cyber incidents.
- Continuous SOC Monitoring: Keep an eye on your networks and systems in real time to catch suspicious activity before it becomes a problem.
- Data Encryption: Protect sensitive information by turning it into unreadable code that only authorized users can access.
- Multi-Factor Authentication (MFA): Add extra layers of verification to make it difficult for cybercriminals to access your accounts.
- Intrusion Detection and Prevention Systems (IDPS): Watch for malicious activity and stop threats before they can cause damage.
- Fostering a Culture of Cyber Resilience: Train your team, raise awareness, and encourage a mindset that keeps security top of mind for everyone.
How Much Cyber Risk Are You Willing To Accept?
There is a common misconception about risk, particularly regarding risk tolerance. In many cases, risk tolerance is reactive rather than proactive. This is a major reason organizations often act only after damage has already occurred. However, this approach must end before the consequences become too severe to reverse. In the critical infrastructure sector, now more than ever, it is essential to maintain a proactive and unwavering stance on risk management.
Thus, the fundamental question remains: how much cyber risk are we truly willing to accept given the catastrophic consequences presented above?
CyberGlobal delivers an extensive suite of risk management solutions, with a wide range of managed cybersecurity services meticulously crafted to empower strategic companies to foresee, mitigate, and master potential threats before they escalate into critical crises. In an era defined by rapidly evolving digital and operational landscapes, organizations can no longer afford a reactive stance; they require forward-thinking, proactive strategies to safeguard their assets, protect their reputation, and ensure operational resilience.

