In recent years, the world’s reliance on networks, digital systems, and information has grown rapidly, and with it, the number and sophistication of threats. Critical infrastructure such as healthcare, transportation, energy systems, and even the military has become a prime target for malicious actors seeking to disrupt, intimidate, or inflict damage for political, ideological, or religious motives. These cyber attacks pose severe risks, aiming to cause financial loss, physical harm, and social disruption, highlighting the urgent need to strengthen cybersecurity frameworks for critical infrastructure.
What is a Cybersecurity Framework for Critical Infrastructure?
For critical infrastructure, a cybersecurity framework is built on coherent guidelines, standards, and best practices designed to help essential organizations minimize cyber risks. Such a framework enables the proactive identification and assessment of potential threats, strengthens overall system security, and ensures an effective response in the event of a cyberattack.
The Role of Cybersecurity for Critical Industries
The critical industries are the foundation of modern society and the threads that keep us interconnected on a global scale. As such, cybersecurity is not only crucial but essential to sustaining our daily operations and lifestyles. Acknowledging how cybersecurity intersects with critical sectors helps us anticipate risks, build stronger defenses, and safeguard the public. The table below outlines several key sectors, why they matter, and how cybersecurity underpins their operations.
| SECTOR | IMPORTANCE | CYBERSECURITY ROLE |
| ENERGY | Power generation, grids, and pipelines that keep lights on, industries running, and essential services operational. | Securing smart grids, power plants, and control systems prevents outages, blackouts, and physical damage. Attacks like the Ukraine Power Grid incident highlight the potential impact. |
| INTERNET | The backbone of modern communication, digital commerce, and information exchange, critical for everyday life and global connectivity. | Protects data integrity, prevents service disruptions, and safeguards sensitive information from cyber espionage and sabotage. |
| TRANSPORT | Systems that facilitate the movement of people and goods, including airports, railways, maritime, and logistics networks. | Ensures the safety and integrity of transportation management systems, traffic control, and logistics networks. Protects against cyber threats that could cause operational disruptions, accidents, or even physical harm, while safeguarding sensitive operational data. |
| GOVT & DEFENSE | National security, public safety, and governance systems that protect sovereignty and citizens. | Defends sensitive data, election systems, and military assets against espionage, sabotage, and cyber warfare |
| HEALTHCARE | Hospitals, medical devices, and health records that safeguard public health and emergency response capabilities | Secures medical devices, patient records, and hospital networks to prevent operational disruptions and protect sensitive health data. |
| RETAIL & E-COMMERCE | Consumer services and supply chains that drive economic activity and guarantee the availability of goods and services. | Protects customer data, payment information, and online transaction systems from theft and fraud. |
Resilience in critical infrastructure depends on people as much as technology. Developing a skilled workforce, enforcing secure-by-default practices, and fostering a culture of accountability turn cybersecurity from a checkbox into a strategic advantage – protecting economies, communities, and the essential services we all rely on.
The 6 Key Pillars of an Effective Cybersecurity Framework
There are six key pillars of an effective cybersecurity framework that, taken together, provide a clear, scalable foundation for protecting assets, managing risk, and sustaining resilience. These pillars help organizations align strategy with controls, balance prevention with detection and response, and adapt to evolving threats without disrupting mission-critical operations.
1. Risk Assessment
In cybersecurity, analyzing the cyber risk vulnerability is the most essential factor that can majorly affect any organization. By taking this first step, we can uncover and evaluate the threats and ensure the safety of essential services.
2. Incident Response Plans
Taking precautions is a good step in preventing cyberattacks, but even then, things can go sideways. Creating an effective incident response plan will minimize the damages and set the organization’s activities to a normal state quickly and securely.
3. Continuous Monitoring (SOC)
Continuous monitoring consists of an ongoing process that analyzes security events, including network activities and log entries, in order to maintain the safety of an organization’s information system. Security operation centers manage to detect and react to threats with the help of professional analysts and, specifically, automated tools.
4. Technological Safeguards
Technological Safeguards are represented by a variation of digital tools designed to restrict unauthorized access, defend against malware, and ensure the integrity of information. Most common examples of technological safeguards contain access controls, firewalls, encryption, and threat detection systems.
5. Human Factors & Awareness
Human Factors and Awareness focus on the human side of security, cultivating a culture where every individual understands their role in protecting information and systems. This includes regular training on phishing and social engineering, clear policies and responsibilities, and practical exercises such as simulations to reinforce safe behaviors.
6. Sector-Specific Adaptation
Sector-Specific Adaptation tailors cybersecurity practices to the unique operational models, regulatory requirements, and threat landscapes of each industry. It aligns controls with mission-critical processes, legacy technologies, safety constraints, and compliance obligations to ensure security measures are both effective and practical.
Want to build a more effective cybersecurity framework and grasp cyber risk in critical sectors? Get our latest Cyber Risk Guide.
The Consequences of Cyberattacks on Critical Infrastructure
The consequences of cyberattacks have escalated to the point where inaction is no longer tenable. These incidents can result in lasting operational disruption, significant financial losses, erosion of trust, and broader societal effects that impact individuals and organizations across multiple domains. To provide analytical clarity, we categorize the impacts of cyberattacks into two groups: direct impacts (immediate, measurable harms) and indirect impacts (secondary, longer-term consequences).
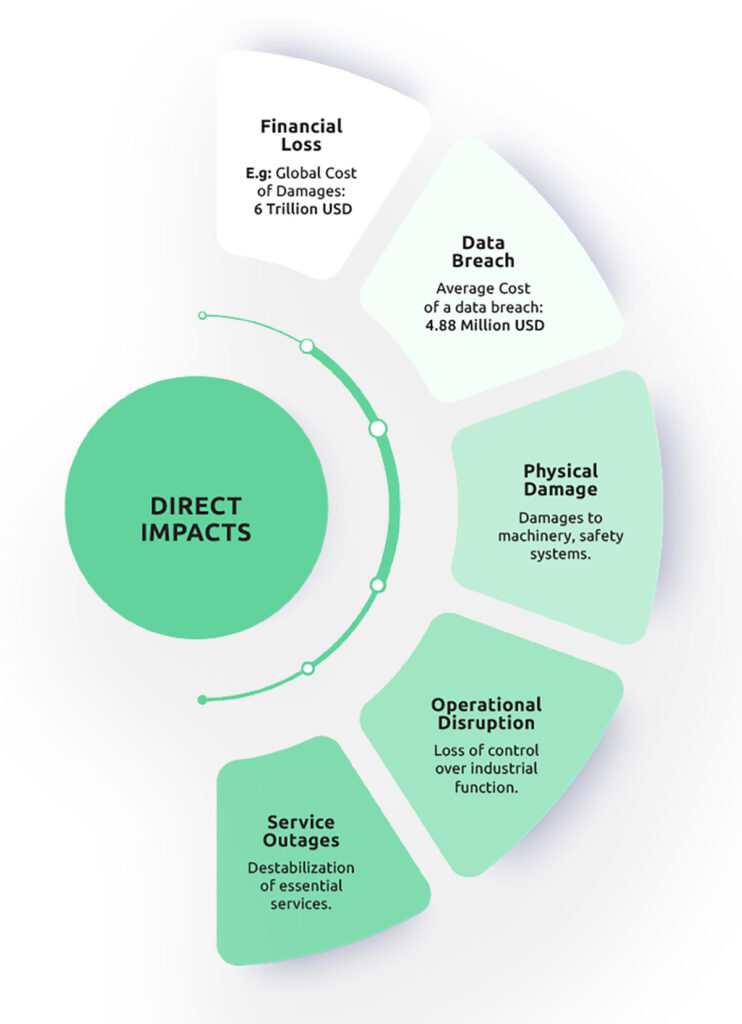
Direct Impacts
Direct impacts constitute the first-order effects of a cyberattack, the immediate, observable consequences that organizations experience at the outset. They are generally tangible, time-bound, and measurable, providing the most direct indicator of the attack’s immediate severity.
- Financial Loss: Immediate costs from incident response, ransom payments, regulatory fines, contract penalties, and lost revenue during downtime.
- Data Breach: Unauthorized access or exfiltration of sensitive information, leading to exposure of personal, financial, or proprietary data.
- Physical Damage: Harm to equipment or facilities caused by cyber-physical attacks.
- Operational Disruption: Interruption of core business processes and supply chains, reducing productivity and delaying deliveries or services.
- Service Outages: Loss of availability for customer-facing or critical services
Indirect Impacts
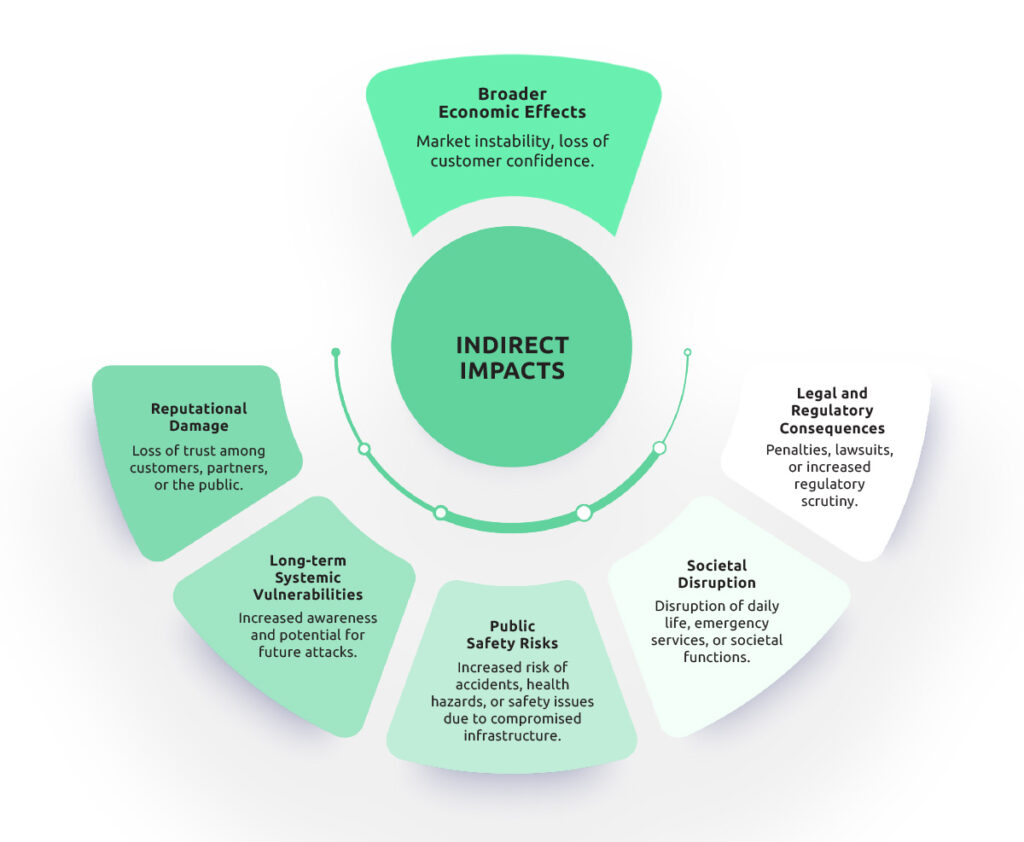
Indirect impacts, by contrast, constitute the aftershock, the second-order effects that emerge after the immediate incident has been contained. Although they manifest over time, these consequences can be equally, or even more, severe than the initial damage. Collectively, these indirect effects can compound and outlast the direct impacts, shaping an organization’s performance and risk posture for years.
- Reputational Damage: Erosion of trust among customers, partners, and investors. Lack of confidence in the market.
- Long-term Systemic Vulnerabilities: Weaknesses revealed by attacks or even introduced by the attacks. Remediations must be taken into account swiftly.
- Public Safety Risks: Heightened threats to health and safety when critical services (e.g., healthcare, energy, water, transportation) are degraded or manipulated post-incident.
- Societal Disruption: Broader community and economic impacts, including supply chain instability, service inequities, and reduced public confidence in essential institutions.
- Legal and Regulatory Consequences: Extended investigations, litigation, settlements, consent decrees, and ongoing compliance obligations that impose financial and operational burdens.
Examples of Cyberattacks on Critical Infrastructure
In our Cyber Risk Guide, we examine a series of cyberattacks spanning the past decade. In each case, the consequences escalated to high or even critical levels, causing significant harm to both industries and society at large. Here are a few cyber incident examples from our guide:
- WannaCry Ransomware: In this particular cyber attack, the world experienced a major shock. The attack crippled hundreds of businesses, affecting the healthcare systems, disrupting critical services, and causing exponential remediation costs..
- NotPetya Attack: From billions of dollars lost to wiped and encrypted data, the NotPetya attack quickly spread chaos with its destructive nature. Shockingly, the attack was meant to disrupt, not ransom.
- Marriott Data Breach: Penalties and reputational damages remain at the center of the cyber attack. Millions of personal data points were compromised, and the indirect impacts quickly became immeasurable.
- Costa Rica GVT Ransomware Attack: National emergency, economic fallout. This type of attack has the ability to destabilize entire societies.
Practical Steps to Improve the Cybersecurity Framework
The cybersecurity framework can be gradually improved following a brief, actionable list. The following quick actions offer a focused roadmap to strengthen cybersecurity in essential industries, from prevention to rapid response.
- Run regular cyber risk assessments and tackle the highest‑risk issues first.
- Keep a living inventory of your assets (devices, applications, and sensitive data)
- Embrace Zero Trust: use MFA, least privilege, and micro‑segmentation.
- Patch quickly. Use risk-based patching and virtual patches for OT where needed.
- Monitor continuously with SIEM and EDR/XDR (and OT-aware tools for industrial environments).
- Test your incident response and recovery plans, and run tabletop exercises.
- Protect backups with offline/immutable copies, and test restores regularly.
- Train people to spot phishing and social engineering, and make reporting issues easy.
- Lock down configurations (CIS baselines) and use allowlisting on critical systems.
- Manage third‑party risk: vet vendors, monitor integrations, and require clear security controls.
CyberGlobal’s Role in Cybersecurity Framework Optimization
At CyberGlobal, we partner with critical infrastructure organizations to build strong, practical cybersecurity programs that actually work day to day. Instead of relying on one-off tools, we take a layered approach that blends technology with clear governance, smart risk management, and real-world resilience. We start by getting to know your environments so we can spot the most important vulnerabilities, prioritize what to fix first, and align security with your business and safety goals.
Our framework emphasizes proactive defense. We conduct penetration testing and threat modeling to simulate real-world attacks and close security gaps before they are exploited. We provide 24/7 threat monitoring and Managed Security Services to deliver continuous protection, rapid detection, and expert triage. When incidents occur, our incident response and disaster recovery capabilities contain threats, mitigate impact, and restore operations quickly to minimize downtime.
This holistic approach ensures your program is not only compliant with sector regulations and standards but also adaptive and resilient against evolving cyber threats—safeguarding your mission, people, and services.

